TrickerBot malware attacks are ramping up ahead of Tax Day
A powerful data-stealing malware campaign with a tax theme is on the rise to target unsuspecting filers ahead of Tax Day.
TrickBot, a financially motivated trojan, infects Windows computers through a malicious Excel document sent by a specially crafted email. Once infected, the malware targets vulnerable devices on the network and combs for passwords and banking information to send back to the attacker. The collected information can be used to steal funds for fraud. The ever-expanding malware is continually developed to collect as many credentials as possible.
By stealing tax documents, the scammers can also file fraudulent end-of-year tax forms to reap the returns. The Internal Revenue said fraudsters scammed the agency out of more than $1.6 million in fraudulent returns during the 2016 tax year.
IBM X-Force researchers say the attackers have begun impersonating emails from three of the largest accounting and payroll providers, including ADP and Paychex, by registering similar-looking domains — known as domain squatting.
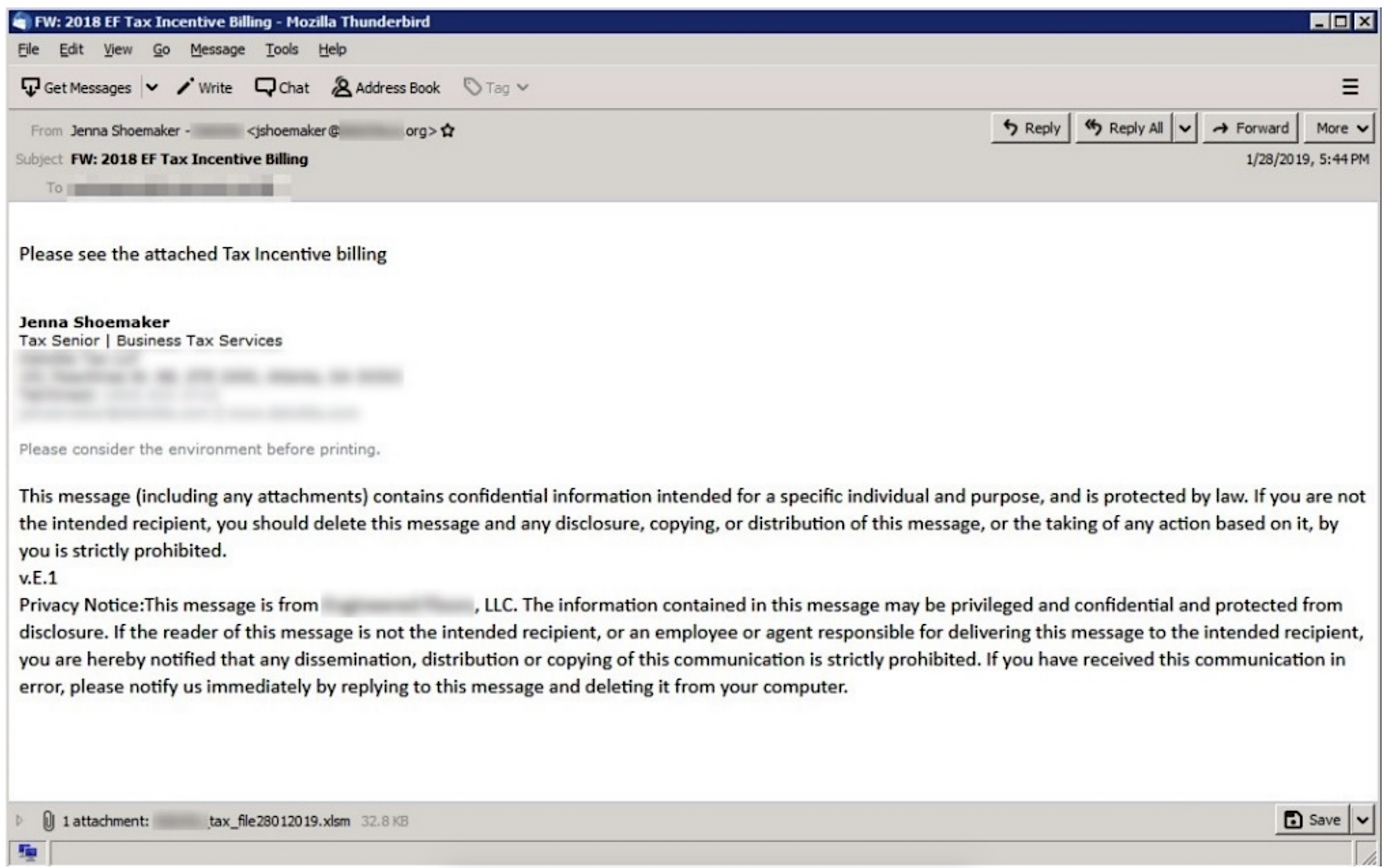
One of the spoofed emails impersonating a payroll provider. (Image: supplied)
“We believe this campaign to be highly targeted in its efforts to infiltrate US organizations, with the hallmarks of the TrickBot Trojan gang,” said Limor Kessem, global executive security advisor at IBM. “Since it emerged in 2016, we’ve seen that TrickBot’s operators focus their efforts on businesses and, therefore, manage distribution in ways that would look benign to enterprise uses: through booby-trapped productivity files and fake bank websites.”
Where TrickBot traditionally focused on business banking and high-value accounts with private banking and wealth management firms, the malware in recent years has expanded to hit cryptocurrency sites and owners.
“This is not a threat of the past,” said Kessem. “Based on our research, not only is TrickBot one of the most prominent organized crime gangs in the bank fraud arena, we also expect to see it maintain its position on the global malware chart, unless it is interrupted by law enforcement in 2019.”
The malware continues to grow, IBM said. Its backend infrastructure has at least 2,400 command and control servers with hundreds of configurations and versions, with infections most common in the U.S. and U.K. — seen as high value regions.
“As cybercriminal gangs of this level continue to gain steam, it’s increasingly important for businesses and consumers to be more aware of their own activity online, even when they’re doing something as simple as clicking on a link in an email,” said Kessem. “Email is an incredibly easy way for an attacker to interact with potential victims, posing as a trusted brand to infiltrate devices and eventually your networks,” she said.
Tax Day is April 15.
from TechCrunch https://tcrn.ch/2U0nO72


No comments
Post a Comment